Introduction
Crack The Hash is a capture the flag game hosted over at TryHackMe. The room presents a series of hashed passwords which you will need to crack in order to obtain the flags. This walk through will crack the first few hashes through free online services, these services can crack a range of common algorithms. More complex hash algorithms will be cracked with Hashcat.
The Crack The Hash game can be found at: https://tryhackme.com/room/crackthehash .
Task 1.1 – MD5
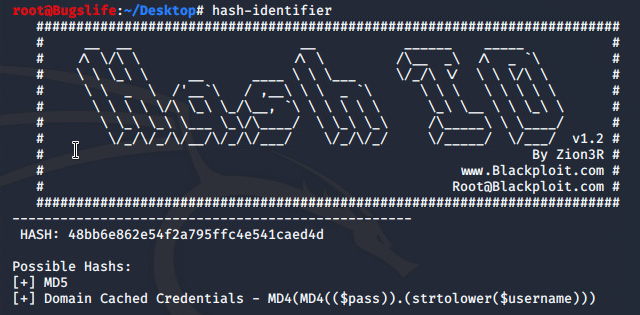
Given hash: 48bb6e862e54f2a795ffc4e541caed4d
“The MD5 message-digest algorithm is a widely used hash function producing a 128-bit hash value. Although MD5 was initially designed to be used as a cryptographic hash function, it has been found to suffer from extensive vulnerabilities. It can still be used as a checksum to verify data integrity, but only against unintentional corruption. It remains suitable for other non-cryptographic purposes, for example for determining the partition for a particular key in a partitioned database.
One basic requirement of any cryptographic hash function is that it should be computationally infeasible to find two distinct messages that hash to the same value. MD5 fails this requirement catastrophically; such collisions can be found in seconds on an ordinary home computer.” *https://en.wikipedia.org/wiki/MD5*
Using kali’s built in tool Hash-Identifier to identify the hash, the tool reveals it is an MD5 hash.
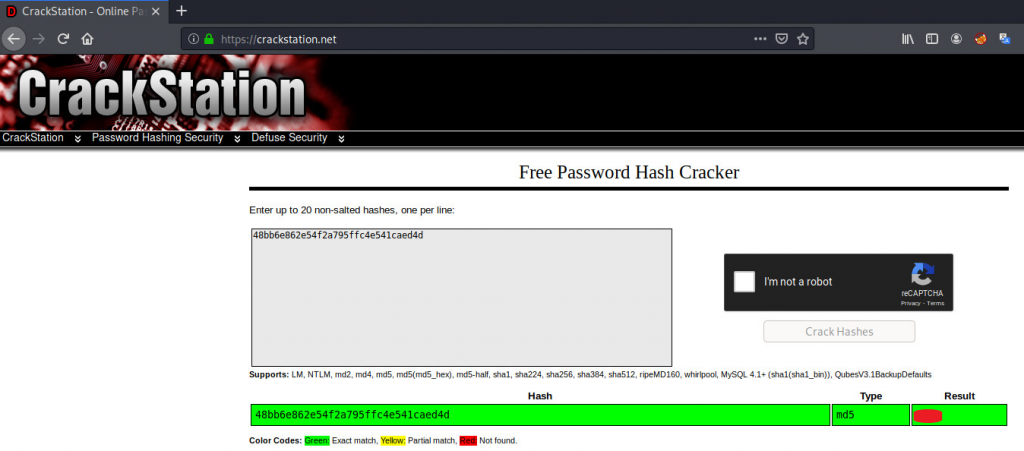
As MD5 is easy to crack and can be done using an online hash cracker. This example below uses the online hash cracker https://crackstation.net to crack the password.
Task 1.2 – SHA1
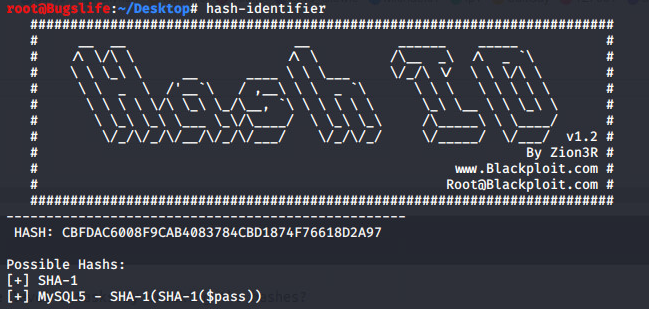
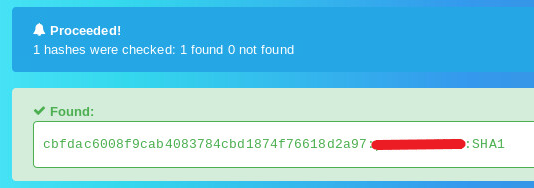
Given hash: CBFDAC6008F9CAB4083784CBD1874F76618D2A97
“In cryptography, SHA-1 (Secure Hash Algorithm 1) is a cryptographic hash function which takes an input and produces a 160-bit (20-byte) hash value known as a message digest – typically rendered as a hexadecimal number, 40 digits long. SHA-1 forms part of several widely used security applications and protocols, including TLS and SSL, PGP, SSH, S/MIME, and IPsec.” *https://en.wikipedia.org/wiki/SHA-1*
Using hash-identifier, SHA-1 is detected:
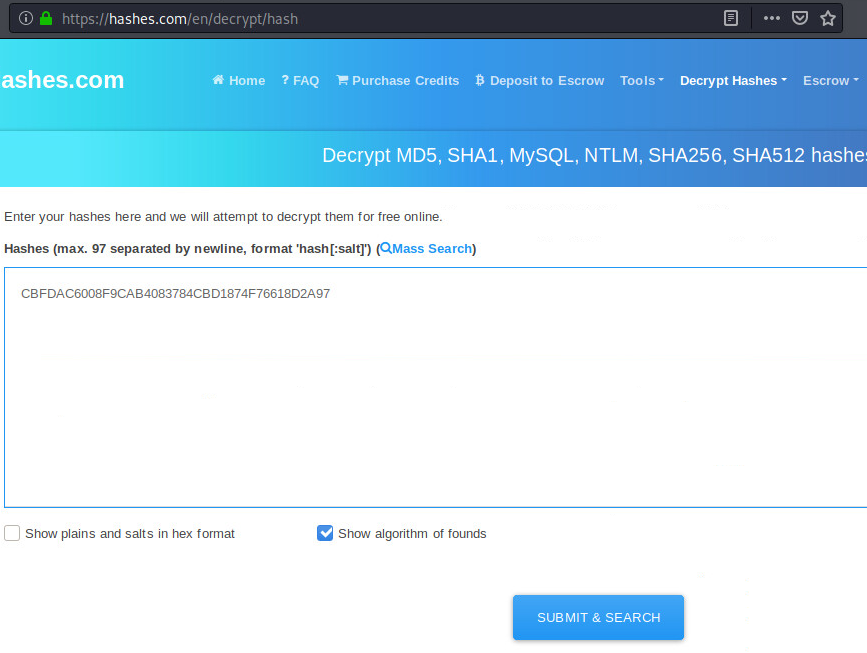
As SHA1 is also easy to crack, an online hash cracker such as https://hashes.com can crack the password.
Task 1.3 – SHA256
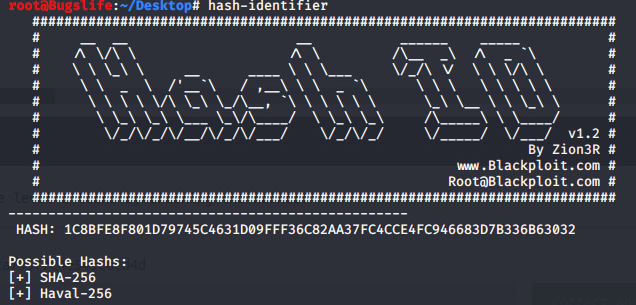
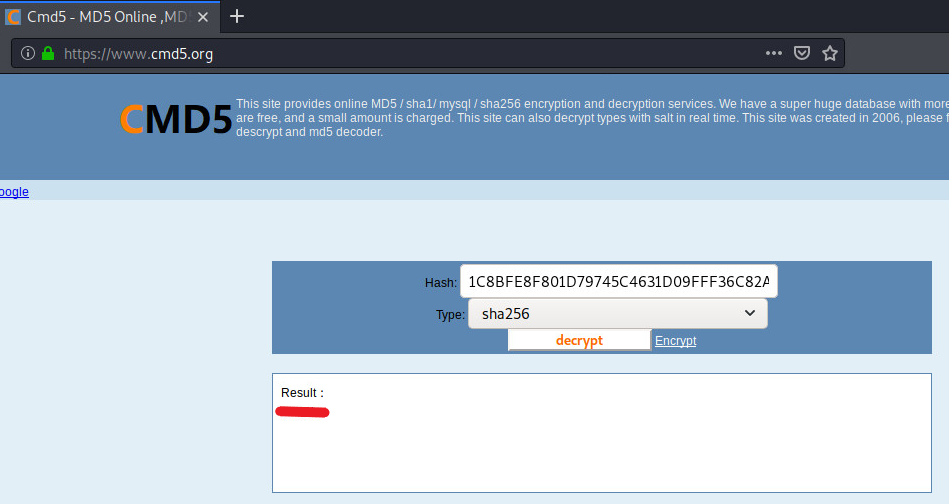
Given hash: 1C8BFE8F801D79745C4631D09FFF36C82AA37FC4CCE4FC946683D7B336B63032
“SHA-2 includes significant changes from its predecessor, SHA-1. The SHA-2 family consists of six hash functions with digests (hash values) that are 224, 256, 384 or 512 bits: SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, SHA-512/256. SHA-256 and SHA-512 are novel hash functions computed with 32-bit and 64-bit words, respectively. They use different shift amounts and additive constants, but their structures are otherwise virtually identical, differing only in the number of rounds.” *https://en.wikipedia.org/wiki/SHA-2*
Hash-Identifier shows this hash as a SHA256 hash.
Although SHA256 is harder to crack due to the increase of the size of the hash, more processing power will be used to crack the hash. Weak passwords will generate the same hashes, due to this flaw a online cracker can be used once again such as https://www.cmd5.org to crack this hash.
Task 1.4 – Blowfish Bcrypt
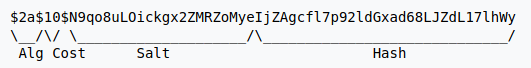
Given hash: $2y$12$Dwt1BZj6pcyc3Dy1FWZ5ieeUznr71EeNkJkUlypTsgbX1H68wsRom
Using a online search engine such as Google, a quick search was made for the first part ($2y$) of the given hash. The first part of this hash tells which type of hash it is. In this case the hash is used in etc/shadow files, The Linux file. This file is used to store the passwords of the users of the linux system. This particular hash is known as a “blowfish bcrypt” hash.
The format of this hash is showcased below.
As I was unable to find an online password cracker able to deal with this type of hash, HashCat was installed and the rockyou.txt password was downloaded from the CrackTheHash Tryhackme site.
Once HashCat was installed the following command was used to start the password cracking.
- Hashcat.exe – the hashcat executable
- -a 0 – the attack mode of straight
- -m 3200 – the hash module of bcrypt blowfish (this is used to tell hashcat the type of password we are dealing with)
- hashinput/crackthehash.txt – the hash stored in a text file.
- Wordlists/rockyou.txt – the wordlist used for the brute-force
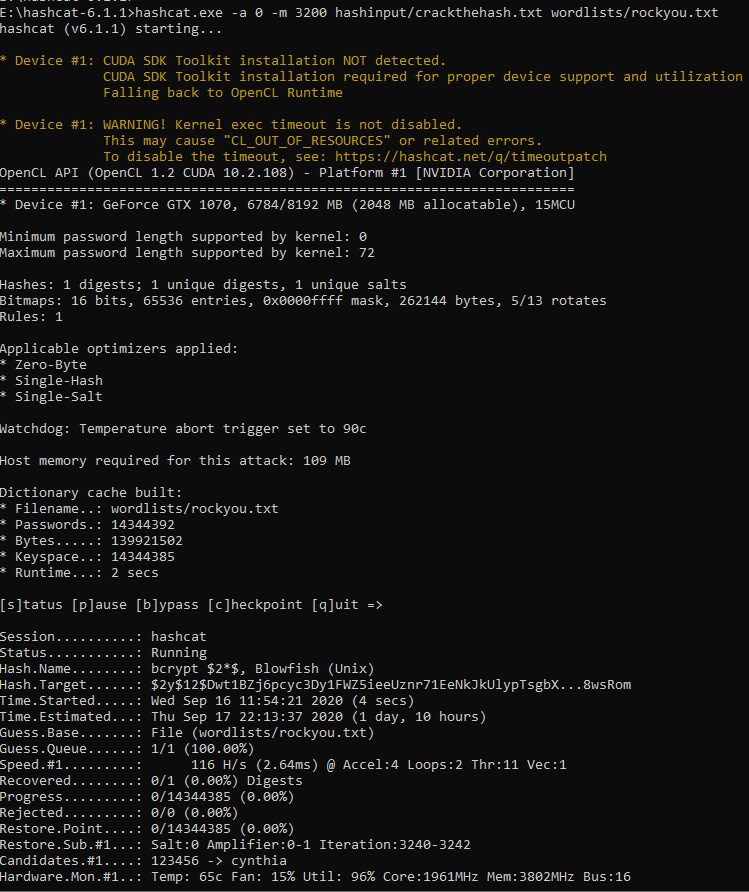
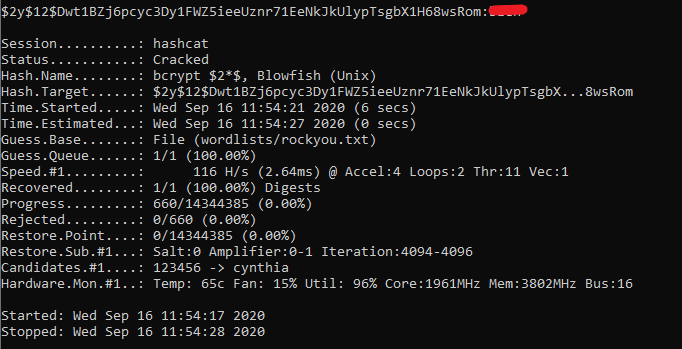
Once the HashCat software was launched the word list was loaded and HashCat began to hash the words within the list and compare with the given hash until a password was found.
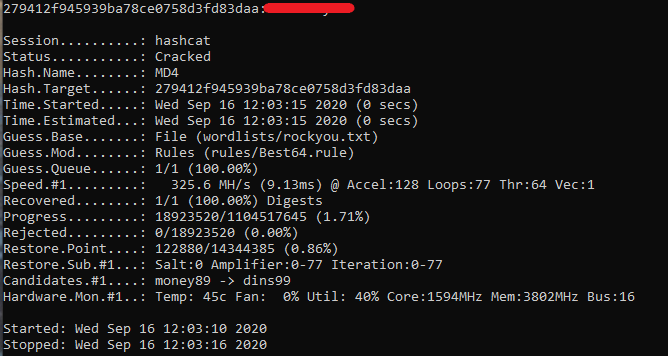
Task 1.5 – MD4
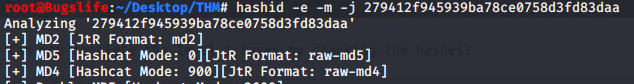
Given hash: 279412f945939ba78ce0758d3fd83daa
“The MD4 Message-Digest Algorithm is a cryptographic hash function developed by Ronald Rivest in 1990. The digest length is 128 bits. The algorithm has influenced later designs, such as the MD5, SHA-1 and RIPEMD algorithms. The initialism “MD” stands for “Message Digest.“ *https://en.wikipedia.org/wiki/MD4*
Although the hashid tool picked up the hash as both MD5 and MD4, I took a call to assume this task would pick a different hash type that was used in task 1.1.
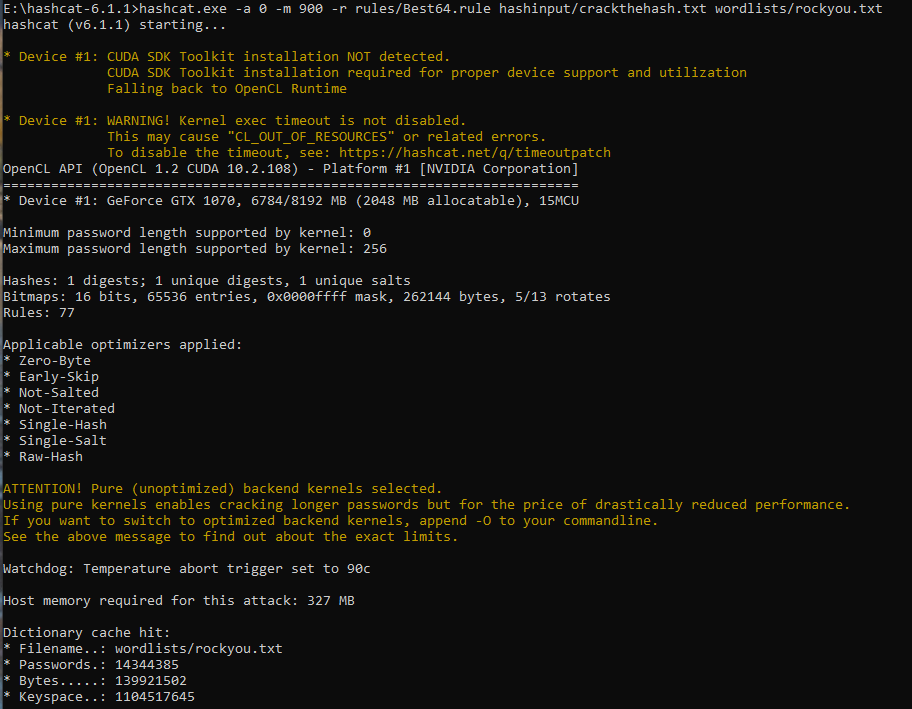
Using HashCat again with the same parameters as before but swapping out the module to 900 to instruct HashCat the hash is a MD4 hash. HashCat gets to work and quickly cracks the hash.
Section Two
As some of the basic hashes have been completed in section one, section two explores harder hashed algorithms with built in brute force protections such as salt. For each one, HashCat is used as the built in modules covers a wide range of hash types for cracking and using GPU to power the cracking provides excellence speed results compared to CPU cracking done via other password crackers such as a john the ripper.
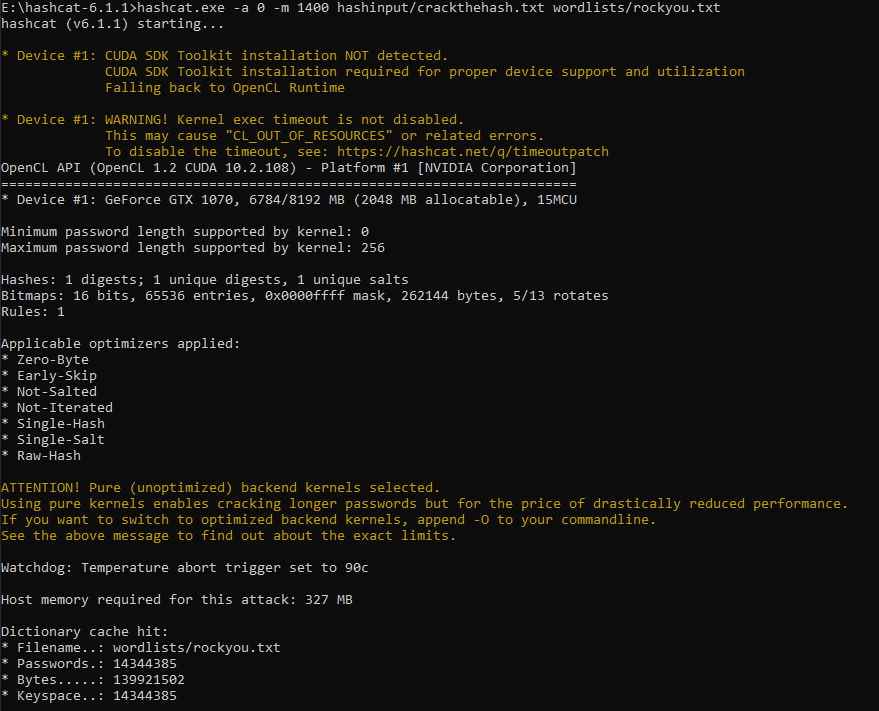
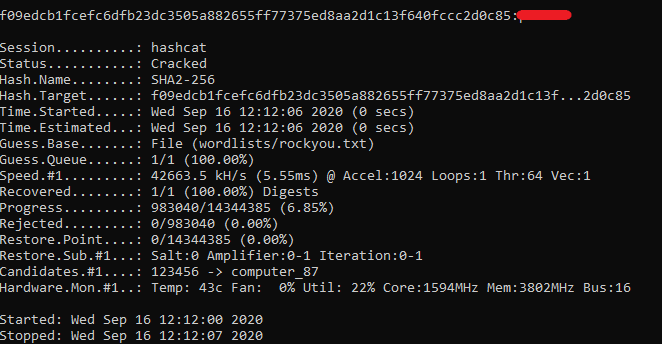
Task 2.1 – SHA256
Given Hash: F09EDCB1FCEFC6DFB23DC3505A882655FF77375ED8AA2D1C13F640FCCC2D0C85
Using hash-identify, the hash is revealed as a SHA2-256 hash.
HashCat is used once again with the SHA2-256 module (-m 1400). The password was cracked quickly due to its weak contents.
Task 2.2 – NTLM
Given hash: 1DFECA0C002AE40B8619ECF94819CC1B
“In a Windows network, NT (New Technology) LAN Manager (NTLM) is a suite of Microsoft security protocols intended to provide authentication, integrity, and confidentiality to users. NTLM is the successor to the authentication protocol in Microsoft LAN Manager (LANMAN), an older Microsoft product. The NTLM protocol suite is implemented in a Security Support Provider, which combines the LAN Manager authentication protocol, NTLMv1, NTLMv2 and NTLM2 Session protocols in a single package. Whether these protocols are used or can be used on a system is governed by Group Policy settings, for which different versions of Windows have different default settings. NTLM passwords are considered weak because they can be brute-forced very easily with modern hardware.” *https://en.wikipedia.org/wiki/NT_LAN_Manager*
Hash-Identifier selects the MD5 or Domain Cached Credentials (NTLM) format for the given hash. As a previous task has already covered MD5, NTLM will be the first option to test.
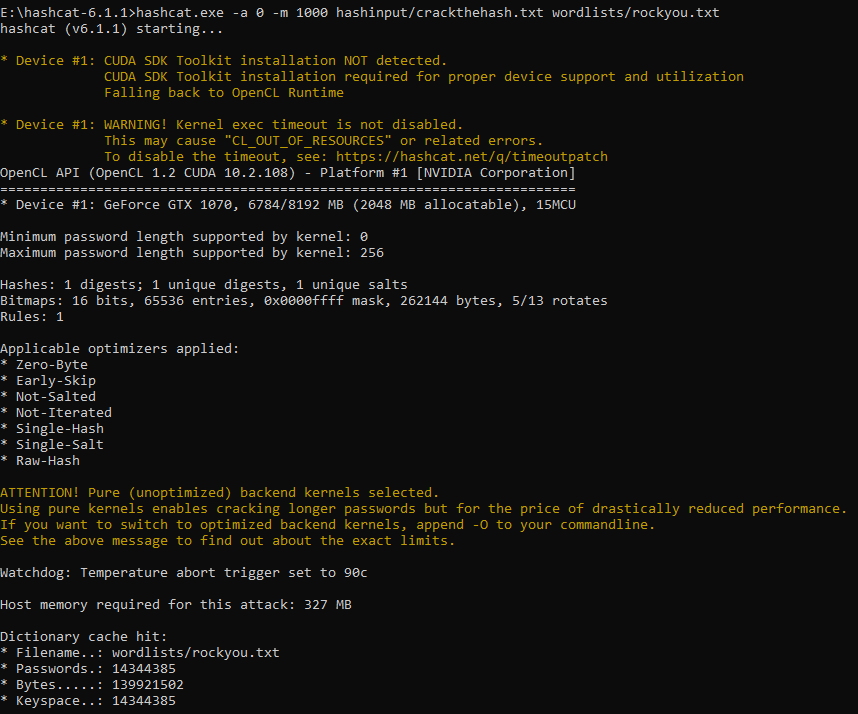
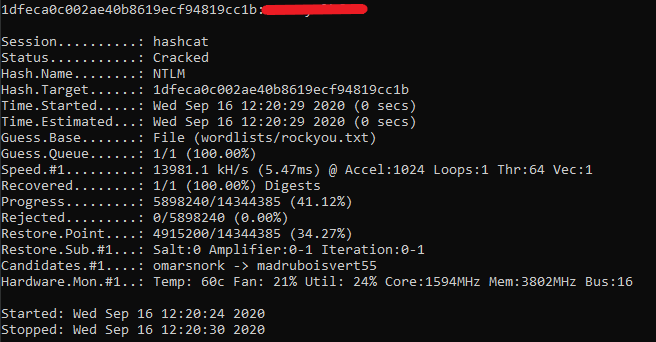
Using the 1000 module (NTLM), the hash was provided to HashCat and cracked fairly quickly, Notice the time frame of 6 seconds 41% of the word list was completed, this indicates that the NTLM algorithm is fairly easy to compute.
Task 2.3 – SHA512Crypt
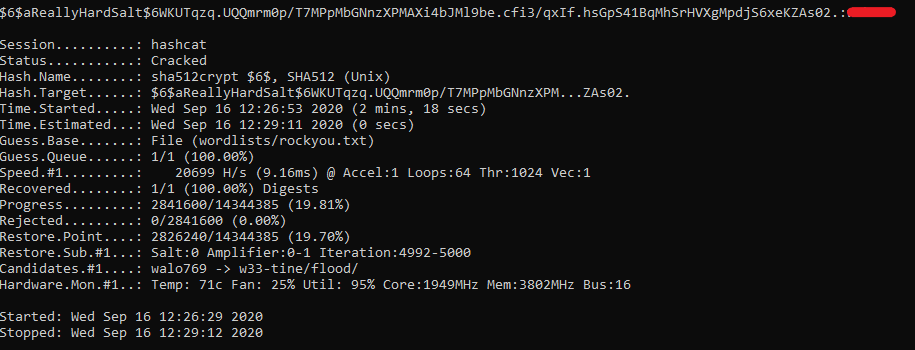
Given hash: $6$aReallyHardSalt$6WKUTqzq.UQQmrm0p/T7MPpMbGNnzXPMAXi4bJMl9be.cfi3/qxIf.hsGpS41BqMhSrHVXgMpdjS6xeKZAs02.
Salt: aReallyHardSalt
Rounds: 5
Using a search engine for the first part of the hash, articles described this hash as SHA512-Crypt hash.
“This class implements the new generation, scalable, SHA512-based Unix ‘crypt’ algorithm developed by a group of engineers from Red Hat, Sun, IBM, and HP for common use in the Unix and Linux /etc/shadow files.” *http://stella.aip.de/javadoc/standard/util/Sha512Crypt.html*
When using HashCat’s built in SHA512Crypt module (1800), HashCat extracted the salt and the rounds from the hash and began cracking the password. Compared to other hashes this hash took longer to calculate each potential password, however eventually the password was cracked.
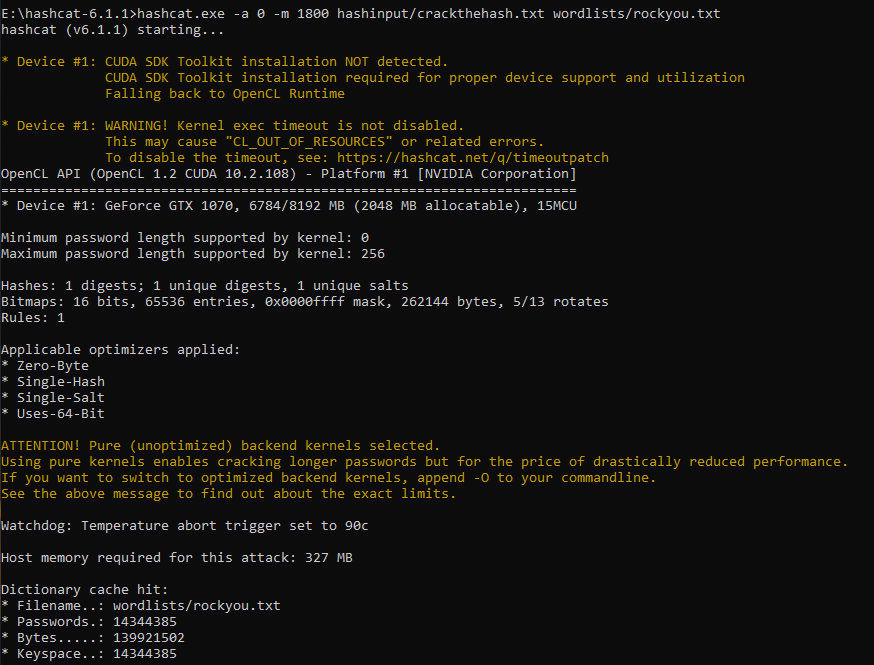
Task 2.4 – SHA1 + Salt
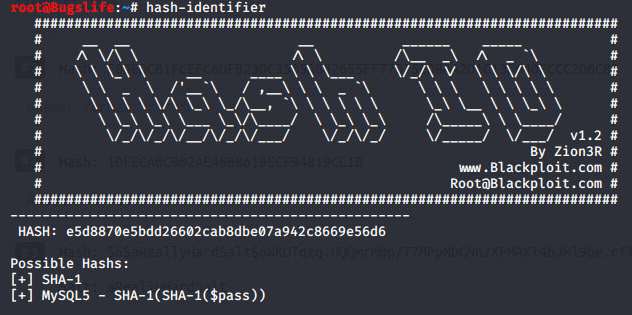
Given Hash: e5d8870e5bdd26602cab8dbe07a942c8669e56d6
Salt: tryhackme
Hash-identifier had identified the hash as a SHA-1 hash. As a salt was supplied, we will assume this will be SHA1 with a salt.
“In cryptography, a salt is random data that is used as an additional input to a one-way function that hashes data, a password or passphrase. Salts are used to safeguard passwords in storage. Historically a password was stored in plaintext on a system, but over time additional safeguards were developed to protect a user’s password against being read from the system. A salt is one of those methods.
A new salt is randomly generated for each password. In a typical setting, the salt and the password (or its version after key stretching) are concatenated and processed with a cryptographic hash function, and the output hash value (but not the original password) is stored with the salt in a database. Hashing allows for later authentication without keeping and therefore risking exposure of the plaintext password in the event that the authentication data store is compromised.” * https://en.wikipedia.org/wiki/Salt_(cryptography)*
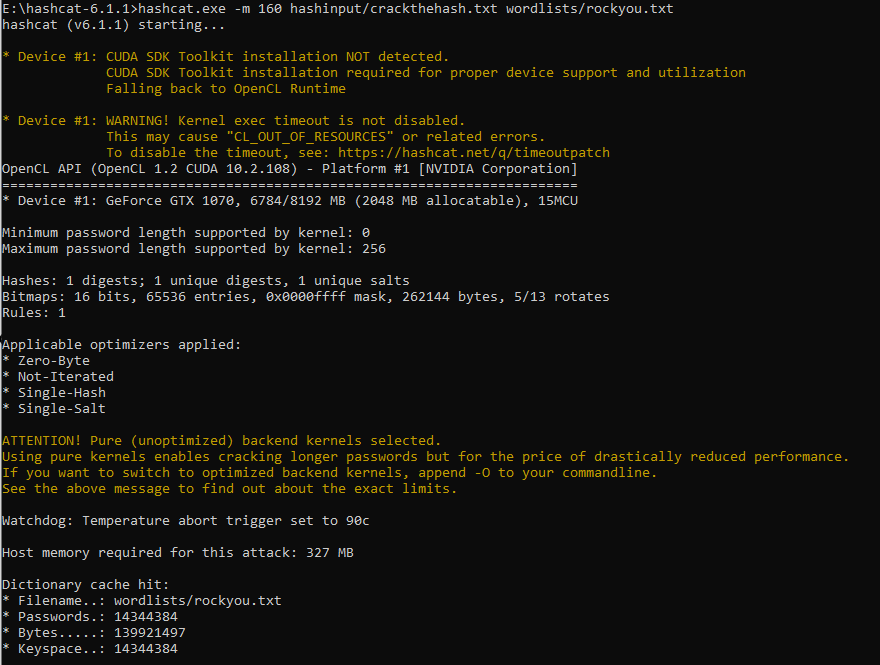
A format of Password:Salt is required for the hash input for HashCat to extract the salt and password correctly.

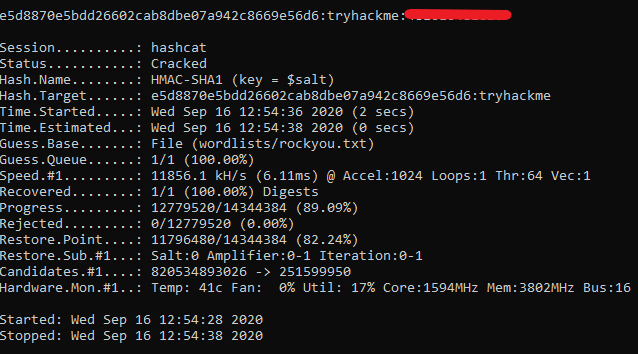
Using -m 160 module of HashCat (HMAC-SHA1), the password and salt is correctly parsed and cracked.
Final Thoughts
Although these algorithms are used to encrypt our passwords its clear that using specialized tools such as HashCat and some processing power, the main weakness is identified in our weak guessable passwords. With the use of word lists and rules within HashCat big lists can capture a frightening number of passwords.
These hashing algorithms have come a long way incorporating built in security such as salts and rounds of encryption to help protect passwords even if the hash was compromised.
Reach out to me via twitter @PR3R00T for any feedback or questions.